Security+ Domain 1 - Zac's Notes
Published at Jul 30, 2025
1. General Security Concepts
These are my notes while studying for the CompTIA Security+ Exam.
1.1
Security Controls
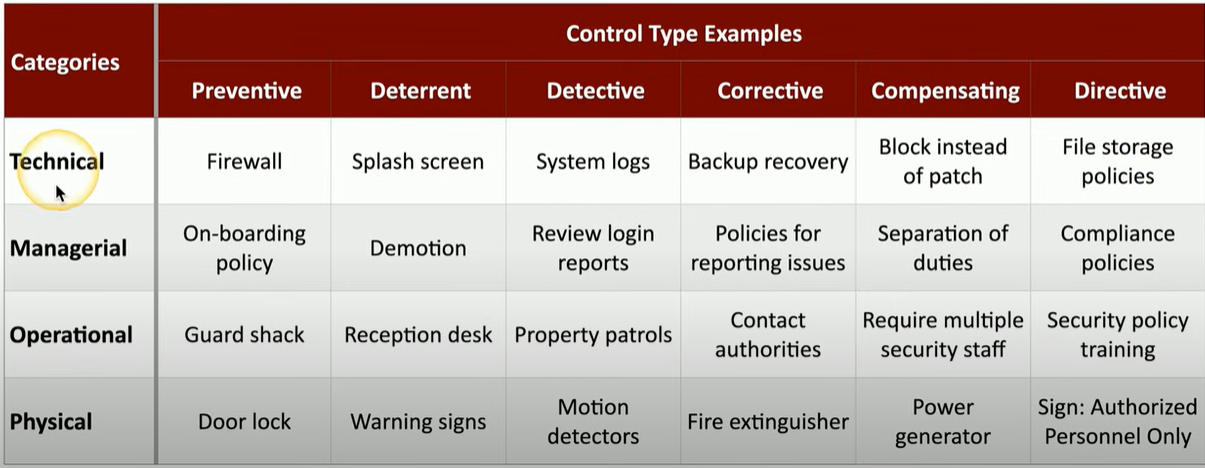
Technical Controls
- Controls implemented using systems
- Operating System Controls
- Firewalls, antivirus
Managerial Controls
- Administrative controls associated with security design and implementation
- Security policies, standard operating procedures
Operational Controls
- Controls implemented by people instead of systems
- Security guards, awareness programs
Physical Controls
- Limit physical access
- Guard shack
- Fences, locks
- Badge readers
Control Types
Preventive
- Blocks access
- Firewall rules
- Follow security policy
- Enable door locks
- Check all identification
Deterrent
- Discourage an intrusion attempt
- Does not directly prevent access
Detective
- Identify and log an intrusion attempt
- May not prevent access
Corrective
- Apply a control after an event has been detected
- Reverse the impact of an event
- Continue operating with minimal downtime
Compensating
- Control using other means
- Existing controls aren’t sufficient
- May be temporary
Directive
- A relatively weak security control
- Direct a subject towards security compliance
1.2
CIA Triad
Confidentiality
Prevent disclosure of information to unauthorized individuals or systems
- Encryption
- Access controls
- Selectively restrict access to a resource (Programmers directory for programmers, etc)
- MFA
Integrity
Messages can’t be modified without detection
- Hashing
- Digital Signatures (Takes a hash and encrypts it asymmetrically to ensure both the file hasn’t been changed and the user are who they say they are)
- Certificates
- Non repudiation
- Proof of integrity
- We can confirm that the information did originate from the intended party
Availability
Systems are up and running
- Redundancy
- Fault tolerance – If one part fails, the whole thing doesn’t fall apart
- Patching
Non-Repudiation
Proof of integrity
Verify data does not change
- In cryptography, we use a hash
- If the data changes, the hash changes
- Doesn’t necessarily verify the user
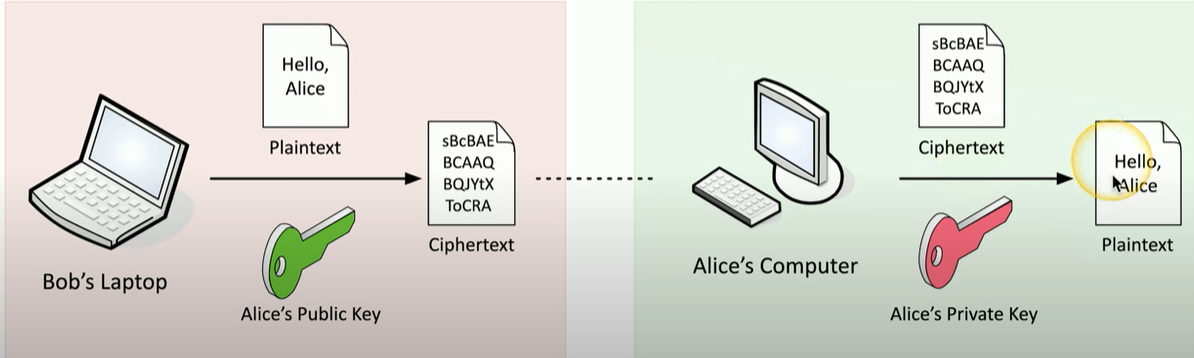
Proof of Origin
Verify the user that sent the data
- Authentication
- Digital Signature
- Private key/Public key
- We know the data is the same, and we know the person is who they were
Creating a digital signature
Verifying a digital signature
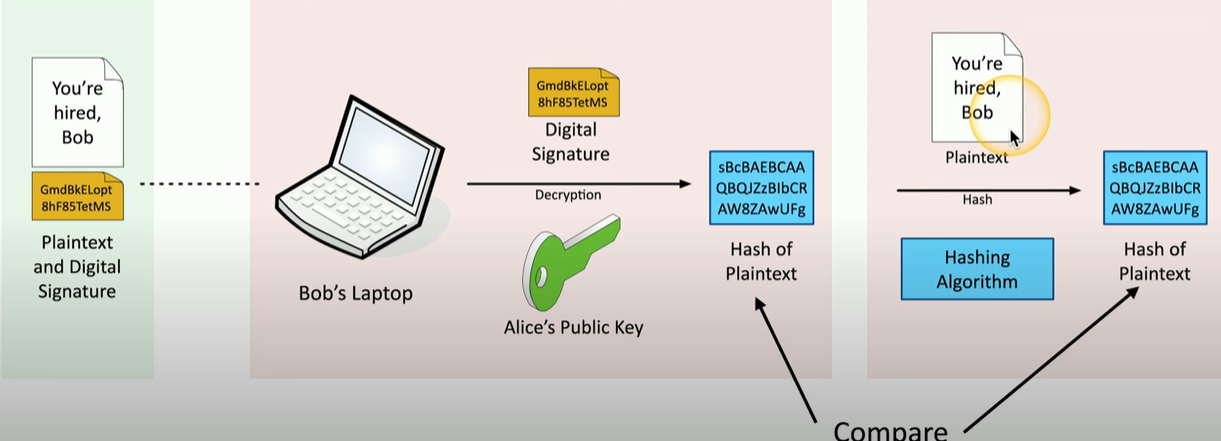
Authentication, Authorization, and Accounting (AAA Framework) !!!
- Prove who we are (Authentication)
- Digitally signed certificate
- Certificate Authority
- Digitally signed certificate
- What access do you have (Authorization)
- Authorization models are often defined by roles, organizations, or attributes
- Active directory is an example of an authorization model
- Resources used (Accounting)
Gap Analysis
- A study of where you are vs where you want to be
- Evaluate people and processes
- Identify weaknesses
- Work toward a known baseline
- Example baseline: The level of employee experience, current training, knowledge of policies and procedures, etc.
- Determine the end goal
- Find the path to get there
Zero Trust
Everything must be verified
- MFA, encryption, system permissions, additional firewalls
- Controlling trust
- Adaptive identity
- Consider the source and the requested resources
- Multiple risk indicators
- Relationship to the organization
- Physical location
- Type of connection
- IP address
- Etc.
- Make the authentication stronger if needed (Especially under suspicious conditions)
- Threat scope reduction
- Reduce the number of possible entry points
- Policy driven access control
- Adaptive identity
- Security zones (Where are you coming from and where are you going, like internal to external, or VPN 1, etc)
- Example: Within the office is implicitly trusted, but at home/abroad is blocked by default
- Policy enforcement point (PEP)
- The gatekeeper
- Any subjects and systems communicating through the network are subject to decisions from the PEP to provide identification of the users and the traffic
- Applying the trust
- Policy Decision Point
- There’s a process for making an authentication decision
- Policy Engine
- Evaluates each access decision based on policy and other information sources
- Grant, deny, or revoke
- Policy Administrator
- Communicates with the Policy Enforcement Point
- Generates access tokens or credentials
- Tells the PEP to allow or disallow access
- Policy Decision Point
Split the network into planes of operation
- Data plane
- Processes the frames, packets, and network data
- Processing, forwarding, trunking, encrypting, NAT
- Control plane
- Manages the actions of the data plane
- Define policies and rules
- Determines how packets should be forwarded
- Routing tables, session tables, NAT tables
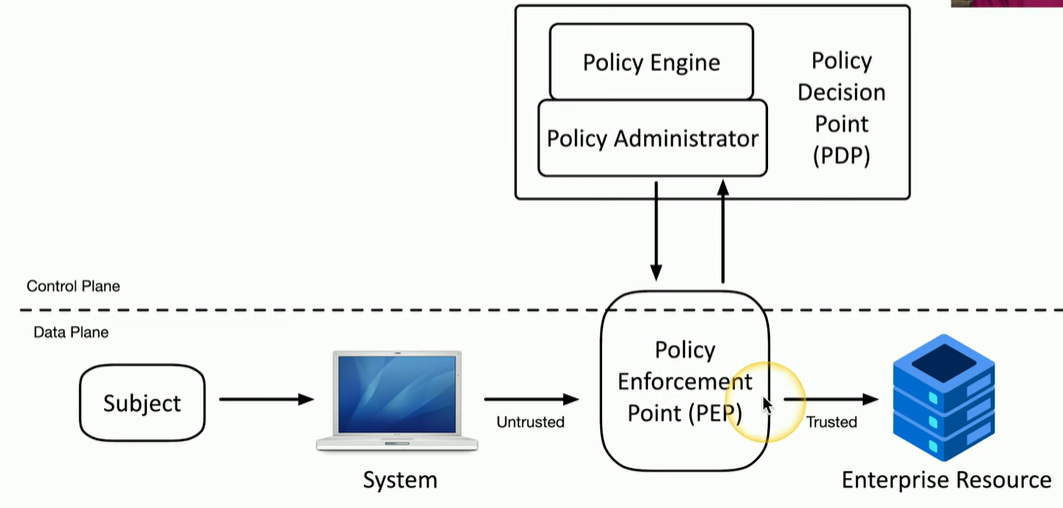
Physical Security
- Barricades, bollards
- Stops people/cars from passing
- Access control vestibules (Like the front entrance at a middle school, outside lock, then verify with the secretary at the desk)
- All doors normally unlocked, opening one door causes others to lock
- All doors normally locked, unlocking one door prevents others from being unlocked
- One door open / the other locked, when one is open, the other cannot be unlocked
- One at a time, controlled groups, managed control through an area
- Fencing
- Very obvious
- Transparent or can be opaque
- Difficult to cut or traverse
- Prevent climbing with barbed wire
- Cameras (CCTV)
- Motion recognition
- Object detection
- Networked and recorded over time
- Security guard
- Physical protection
- Validates identification of employees
- Access badge worn at all times with picture and name, electronically logged
- Two person integrity so no single person has access without supervision
- Lighting
- More light usually means more security
- Especially with cameras
- Sensors
- Infrared for both light and dark
- Motion detectors
- Pressure sensors
Deception and Disruption
Honeynets
- A network of honeypots (Servers, workstations, routers, switches, firewall)
- Honeyfiles (Files with fake information)
- Alerts are sent when people access these
- Honeytokens
- Track malicious actors
- Ex: API Creds, fake email addresses, database records, cookies
1.3
Change Management
- Upgrade Software, patch an application, change firewall configuration, modify switch ports
- One of the most common risks in the enterprise
- Often overlooked or ignored
- Have clear policies
- Frequency, duration, installation, rollback
- Ownership
- Stakeholders
- Who is impacted by this change?
- Impact analysis
- Sandbox testing environment
- Backout plan
-In case things go wrong *ahem Crowdstrike ahem*
- Backups/ways to revert
- Maintenance window
Technical Change Management
- Allowlist / deny list
- Dependencies
- To complete A, you must first complete B
- Version control
1.4
Public Key Infrastructure (PKI)
- Digital Certificates
- Create, distribute, manage, store, revoke
- Symmetric Encryption
- A single, shared key
- Asymmetric Encryption
- Public Key Cryptography
- Private Key
- Public key
- Anyone can see this key, it is given away
- Public key encrypts data, but the private key is the only key that can decrypt it

Key Escrow
- Someone else holds your decryption keys
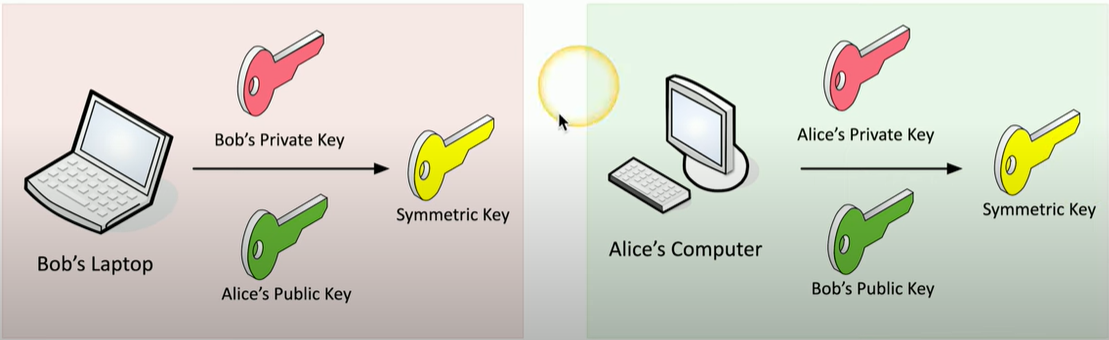
Key Exchange
- Use asymmetric encryption to deliver a symmetric key
- Use public and private keys to create a symmetric key
Encryption Tehcnologies
- Encrypting stored data
- Data at rest: SSD, hard drive, USB drive, cloud storage, etc
- Full disk and partition/volume encryption: BitLocker, FileVault, etc
- File encryption
- EFS (Encrypting File System), third party utilities
- Database encryption
- Protecting stored data and the transmission of that data
- Transparent encryption
- Encrypt all database information with a symmetric key
- Record-level encryption
- Encrypt individual columns
- Use separate symmetric keys for each column
- Transport encryption
- Protect data traversing the network
- Encrypting in the application (HTTPS)
- VPN (Virtual Private Network)
- Encrypts all data transmitted over the network, regardless of the application
- Client based VPN using SSL/TLS
- Site to site VPN using IPsec
Trusted Platform Module (TPM)
- Cryptography hardware on a device
- A cryptographic processor
- Random number generator, key generators
- Persistent memory
- Unique keys burned in during manufacturing
- Versatile memory
- Storage keys, hardware configuration information
- Securely store BitLocker keys
- Password protected
Hardware Security Module (HSM)
- Used in large environments
- Clusters, redundant power
- Securely store thousands of cryptographic keys
- High end cryptographic hardware
- Plug-in card or separate hardware device
Key management system – (Tools like Key Manager Plus)
- Manage all keys from a centralized manager and one console
Secure Enclave
- A protected area for our secrets
- Often implemented as a hardware processor isolated from the main processor
- Provides extensive security features
- Has its own boot ROM
- Monitors the system boot process
- True random number generator
- Real-time memory encryption
- Root cryptographic keys
- Performs AES encryption in hardware
Obfuscation
- Making something unclear but not impossible to understand if you know how to read it
- Steganography
- “Security through obscurity”
- Data Masking
- Credit card: ****2512
Hashing and Digital Signatures
- Like a fingerprint
- Impossible to recover the original message
- Can be a digital signature
- Used for Authentication, Non-Repudiation, Integrity
- Salt
- Random strings added to a hash to further randomize
- Digital Signature
- A message is hashed and then the hash is encrypted with A’s private key, which means that the Digital Signature could only have been made by A. On the other side, the digital signature is decrypted by A’s public key, and then compared to the hash of the received plaintext. The two should match, and confirms that it really came from Alice and wasn’t altered.
Blockchain
- A distributed ledger
- Keep track of transactions
- Everyone on the blockchain network maintains the ledger
- Records and replicates to anyone and everyone 1) A transaction is requested 2) The transaction is sent to every node to be verified 3) The verified transaction is added to a new block of data containing other recently verified transactions 4) A hash is calculated from the previous blocks and added to the new block of verified transactions 5) The block is added to the end of the Blockchain, which is then updated to all nodes in the network for security. The transaction is complete If any blocks are altered, its hash and al the following hashes in the chain are recalculated and will no longer match the rest of the chains and will be rejected
- Practical Applications:
- Payment processing
- Digital identification
- Supply chain monitoring
- Digital voting
Certificates
- Adds trust
- X.509 certificate
- Standard format
- Wildcard certificates (*.google.com)
- Subject Alternative Name (SAN)
- Extension to an X.509 certificate
- Lists additional identification information
- Allows a certificate to support many different domains
- Subject Alternative Name (SAN)
- Key revocation
- Certificate Revocation List (CRL)
- Maintained by the CA
- April 2014 – CVE-2014-0160
- Heartbleed
- OpenSSL flaw put the private key of affected web servers at risk
- OpenSSL was patched, every web server certificate was replaced
- Older certs were moved to the CRL
- Certificate Revocation List (CRL)
- OCSP Stapling
- Online Certificate Status Protocol (OCSP)
- Due to scaling difficulties, the certificate holder verifies their own status
- Stored on the cert holder’s server
- OCSP status is staple into the SSL/TLS handshake
- Digitally signed by the CA
- The browser can check certificate revocation
- More efficient than downloading a CRL
- Due to scaling difficulties, the certificate holder verifies their own status
- Online Certificate Status Protocol (OCSP)