VERE - Rev-2 - Macro
Published at Mar 1, 2025
This Excel document has a VBA macro in it. Use oletools to extract the source code, and then reverse it to get the flag. Note that there is one unprintable character that oletools will not extract right, so your final flag may be missing a single character (but it should be obvious).
First Step: Analyzing the Document with Oletools
The first step is to download the document and use oletools to analyze it. Oletools is a set of tools designed to analyze OLE files, including Microsoft Office documents.
Run the following command to extract the VBA macros:
olevba Book1.xlsmThe result looks like this, which I’ve pasted the relevant parts in code form below:
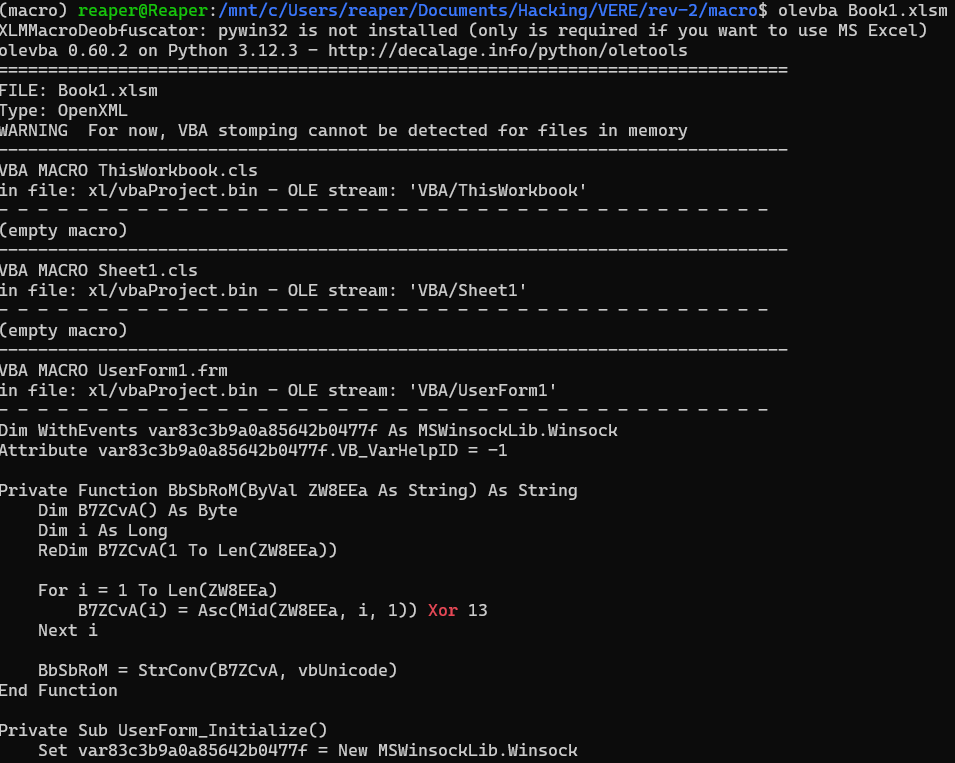
VBA MACRO UserForm1.frm
in file: xl/vbaProject.bin - OLE stream: 'VBA/UserForm1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Dim WithEvents var83c3b9a0a85642b0477f As MSWinsockLib.Winsock
Attribute var83c3b9a0a85642b0477f.VB_VarHelpID = -1
Private Function BbSbRoM(ByVal ZW8EEa As String) As String
Dim B7ZCvA() As Byte
Dim i As Long
ReDim B7ZCvA(1 To Len(ZW8EEa))
For i = 1 To Len(ZW8EEa)
B7ZCvA(i) = Asc(Mid(ZW8EEa, i, 1)) Xor 13
Next i
BbSbRoM = StrConv(B7ZCvA, vbUnicode)
End Function
Private Sub UserForm_Initialize()
Set var83c3b9a0a85642b0477f = New MSWinsockLib.Winsock
var83c3b9a0a85642b0477f.LocalPort = 1234
var83c3b9a0a85642b0477f.Listen
End Sub
Private Sub sock_ConnectionRequest(ByVal varbd4457e7ae1596ff36f4 As Long)
var83c3b9a0a85642b0477f.Close
var83c3b9a0a85642b0477f.Accept varbd4457e7ae1596ff36f4
End Sub
Private Sub sock_DataArrival(ByVal vard39899bc39a205c1095d As Long)
Dim var87a627684d04314c5def As String
var83c3b9a0a85642b0477f.GetData var87a627684d04314c5def, varb5a4ab29b30105b8ecf4
If var87a627684d04314c5def = Chr(BbSbRoM("Jd``h-yeh-kalj,,")) Then
var83c3b9a0a85642b0477f.SendData Chr(BbSbRoM("{hhv{lhk5on8l?h8no9;>h5n4k?>o<<<<ihln?<9>5l4;<><ok<o9h<44i;nonki;:p"))
var83c3b9a0a85642b0477f.Close
End If
End Sub
Private Sub CommandButton1_Click()
UserForm1.Show
End Sub
-------------------------------------------------------------------------------
VBA MACRO Module1.bas
in file: xl/vbaProject.bin - OLE stream: 'VBA/Module1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Sub auto_run()
MsgBox ("I told you not to open random Office documents!! Maybe I put malware in here....")
End Sub
-------------------------------------------------------------------------------
VBA FORM STRING IN 'xl/vbaProject.bin' - OLE stream: 'UserForm1/o'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
�CommandButton1
-------------------------------------------------------------------------------
VBA FORM Variable "b'CommandButton1'" IN 'xl/vbaProject.bin' - OLE stream: 'UserForm1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - The output shows the VBA macros embedded in the document. Just glancing through, I see a lot of obfuscated functions and variables, and a couple event handlers. There’s also a macro named auto_run in Module1 that displays a message box with a note from the challenge author: "I told you not to open random Office documents!! Maybe I put malware in here...." Oh boy.
Deobfuscating the Code
I can’t make heads nor tails of it in its current state, so in order to make the code easier to understand I renamed the variables and functions:
VBA MACRO UserForm1.frm
in file: xl/vbaProject.bin - OLE stream: 'VBA/UserForm1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Dim WithEvents WinsockControl As MSWinsockLib.Winsock
Attribute WinsockControl.VB_VarHelpID = -1
Private Function DeobfuscateString(ByVal ObfuscatedString As String) As String
Dim ByteArray() As Byte
Dim i As Long
ReDim ByteArray(1 To Len(ObfuscatedString))
For i = 1 To Len(ObfuscatedString)
ByteArray(i) = Asc(Mid(ObfuscatedString, i, 1)) Xor 13
Next i
DeobfuscateString = StrConv(ByteArray, vbUnicode)
End Function
Private Sub UserForm_Initialize()
Set WinsockControl = New MSWinsockLib.Winsock
WinsockControl.LocalPort = 1234
WinsockControl.Listen
End Sub
Private Sub sock_ConnectionRequest(ByVal RequestID As Long)
WinsockControl.Close
WinsockControl.Accept RequestID
End Sub
Private Sub sock_DataArrival(ByVal BytesTotal As Long)
Dim ReceivedData As String
WinsockControl.GetData ReceivedData, vbString
If ReceivedData = Chr(DeobfuscateString("Jd``h-yeh-kalj,,")) Then
WinsockControl.SendData Chr(DeobfuscateString("{hhv{lhk5on8l?h8no9;>h5n4k?>o<<<<ihln?<9>5l4;<><ok<o9h<44i;nonki;:p"))
WinsockControl.Close
End If
End Sub
Private Sub CommandButton1_Click()
UserForm1.Show
End Sub
-------------------------------------------------------------------------------
VBA MACRO Module1.bas
in file: xl/vbaProject.bin - OLE stream: 'VBA/Module1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
-- Sub auto_run()
-- MsgBox ("I told you not to open random Office documents!! Maybe I put malware in here....")
-- End Sub
-------------------------------------------------------------------------------
VBA FORM STRING IN 'xl/vbaProject.bin' - OLE stream: 'UserForm1/o'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
�CommandButton1
-------------------------------------------------------------------------------
VBA FORM Variable "b'CommandButton1'" IN 'xl/vbaProject.bin' - OLE stream: 'UserForm1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
NoneDeobfuscating the Strings
The main function that stuck out to me while I was going through this code was the BbSbRoM function (which due to it’s behavior I decided to name DeobfuscateString). This function is used to deobfuscate strings in the code by XORing each character with 13. We can use this function to reveal the hidden messages.
Isolate the DeobfuscateString Function
To safely deobfuscate the strings, I isolated the DeobfuscateString function and created a custom macro using it’s functionality:
Private Function DeobfuscateString(ByVal ObfuscatedString As String) As String
Dim ByteArray() As Byte
Dim i As Long
ReDim ByteArray(1 To Len(ObfuscatedString))
For i = 1 To Len(ObfuscatedString)
ByteArray(i) = Asc(Mid(ObfuscatedString, i, 1)) Xor 13
Next i
DeobfuscateString = StrConv(ByteArray, vbUnicode)
End Function
Sub TestDeobfuscation()
Dim obfuscatedString1 As String
Dim obfuscatedString2 As String
Dim deobfuscatedString1 As String
Dim deobfuscatedString2 As String
obfuscatedString1 = "Jd``h-yeh-kalj,,"
obfuscatedString2 = "{hhv{lhk5on8l?h8no9;>h5n4k?>o<<<<ihln?<9>5l4;<><ok<o9h<44i;nonki;:p"
deobfuscatedString1 = DeobfuscateString(obfuscatedString1)
deobfuscatedString2 = DeobfuscateString(obfuscatedString2)
MsgBox "Deobfuscated String 1: " & deobfuscatedString1 & vbCrLf & _
"Deobfuscated String 2: " & deobfuscatedString2
End SubNote that there are two obfuscatedStrings, and within the second one lies the unprintable character that was mentioned in the chall description, so I think that I’m on the right track here. This doesn’t display well in the markdown, but it appears as whitespace between the the h’s in obfuscatedString2:
obfuscatedString2 = "{hhv{lhk5on8l?h8no9;>h5n4k?>o<<<<ihln?<9>5l4;<><ok<o9h<44i;nonki;:p"The TestDeobfuscation macro will display the deobfuscated strings in a message box, without having to worry about any potential malware that may or may not have been put into the file (After reading the code thoroughly, we know that the auto_run function could raise red flags in another situation but looks innocent here, but Winsock control on port 1234 could indicate a backdoor or listener of some sort. However, due to the nature of the challenge it is unlikely to be actually malicious but it is good practice to identify and diffuse those anyways)
Running My Clean Macro
On a network segmented virtual machine, I opened a new Excel document, hit Alt + F11 to open the VBA editor, and inserted a new module consisting of the DeobfuscateString function and the TestDeobfuscation macro listed above. Then I ran the macro by going to Run > Run Sub/UserForm, which gave me the flag in the following popup message:
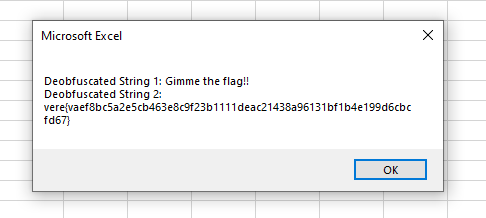
Flag:
vere{vaef8bc5a2e5cb463e8c9f23b1111deac21438a96131bf1b4e199d6cbcfd67}